Hacking Team Spyware Linked to Chrome Zero-Day Attack

Chrome Zero-Day Exploit Linked to Italian Spyware Vendor
A sophisticated zero day vulnerability in Google Chrome was recently exploited in a targeted cyber espionage campaign. Security researchers, including those from Kaspersky, discovered that the attack utilized spyware developed by Memento Labs. Memento Labs is the successor company to the infamous Italian commercial surveillance vendor, Hacking Team. This incident highlights the ongoing threat posed by government aligned threat actors using commercially available offensive tools across the globe.
The Sandbox Escape Vulnerability
The vulnerability, tracked as CVE-2025-2783, was a serious flaw in Google Chrome’s sandbox protection system. The core of the issue was a sandbox escape flaw within Chrome’s Mojo inter process communication (IPC) framework. This framework manages data exchange between different browser components. The flaw allowed attackers to bypass the crucial security boundary.
Attack Mechanism
The campaign, dubbed Operation ForumTroll, began with a classic social engineering trick. Targets received personalized phishing emails containing malicious links. The victims were often lured with invitations to a specific forum. Simply clicking the malicious link was enough to initiate the compromise. It required no further user interaction. Once opened in Chrome, the exploit bypassed the sandbox. This granted the attackers high level code execution privileges on the victim’s machine.
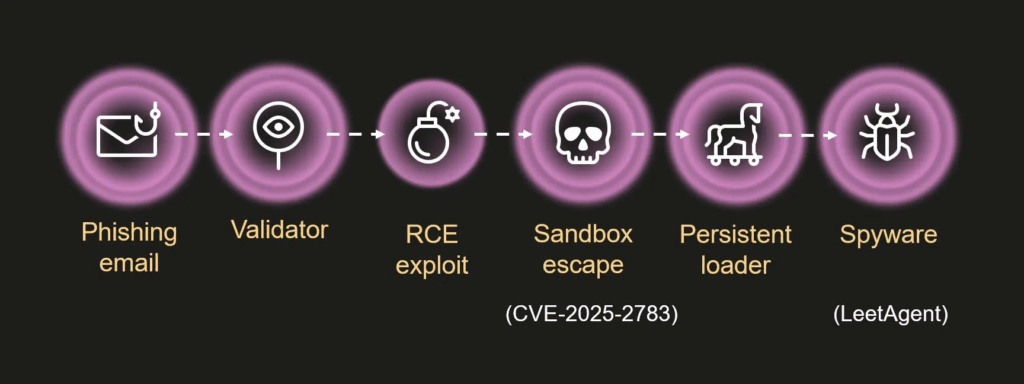
Spyware Traced to Hacking Team’s Successor
Crucially, researchers successfully linked the deployed malicious tools to Memento Labs. Memento Labs was formed following the merger of Hacking Team. Hacking Team was a controversial company known for selling intrusion and surveillance software to governments worldwide.
- Deployed Payloads: The attackers deployed a persistent malware loader which launched a spyware payload known as LeetAgent. This spyware was capable of keylogging, monitoring clipboard data, and stealing files such as .docx, .pdf, and .xlsx.
- Dante Spyware Link: The LeetAgent spyware was also linked to Dante, a more advanced commercial surveillance tool. Dante was developed by Memento Labs as a replacement for the older Remote Control Systems (RCS). The shared code and tradecraft confirmed that the same actor or toolset was behind both the zero day exploitation and the Dante spyware attacks.
The campaign’s primary purpose was espionage. It targeted high profile organizations in specific nations, including media outlets, educational institutions, government organizations, and financial institutions.
Immediate Action Required
Google quickly acknowledged the issue reported by Kaspersky. They subsequently released a security patch for the vulnerability. All users across the globe must immediately update their Google Chrome browser to the latest version. Specifically, updates to Chrome versions 134.0.6998.177 and higher contain the necessary fix. This critical update prevents attackers from exploiting the sandbox escape flaw and installing the powerful spyware.






